Back in April I pressed my older Shuttle SK41G small-form factor system out of mothballs and loaded up Win 7. New (borrowed) life for the Shuttle SK41G
Overall the process went fairly smoothly though the limited feature sets of the core processor presented challenges.
As a system running x32 bit Windows 7 OS and only purposed for visiting guests to our household to use, it seemed to be adequate. I don’t have a PATA-based DVD-ROM reader to allow me to easily load various Linux LiveCD’s that are DVD sized.
I can use some other tools to try to run them via USB, but Shuttle booting off USB drives (or emulators) is a bit hit-or-miss. So for now I continue to test Linux distros that are CD-sized to experiment with performance.
Anyway…I was updating the system last weekend (more on that later) and Malwarebytes notified me there was a new version build available.
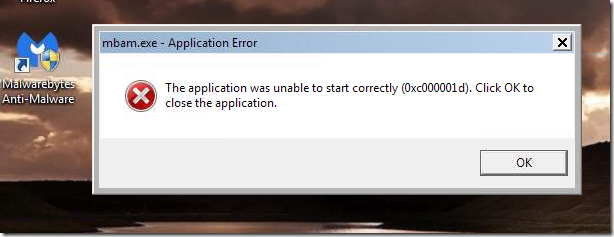
I manually downloaded the installer file, then launched when done and was greeted by this error
mbam.exe – Application Error
The application was unable to start correctly (0x000001d). Click OK to close the application.
That was unexpected. Maybe my installer file was corrupted? I tried a few more download/reinstall attempts but was met with the same error. The previous version worked fine. What gives?
Some web searching led me to this post that detailed the problem and the fix (though the steps didn’t seem clear to me at first reading).
- 0xc000001d error - failed to initialize - Malwarebytes Anti-Malware Help - Malwarebytes Forum
Per “Root Admin”, “This is due to a compatibility issue with some older processors (Single core PIII and earlier, and AMD XP+)” and appeared to arise with version 2.18.
The instructions state the following:
If you are receiving this error, luckily there is a special installer that you can use to avoid the problem. Please download the special installer from this page. Once downloaded, simply double-click to run, and the program should install as normal.
So in my mind, that meant first running the “special installer” and getting a full MBAM installation done.
Nope.
What it means is to do the following;
- Download and install the Malwarebytes/Malwarebytes-Free application and install it.
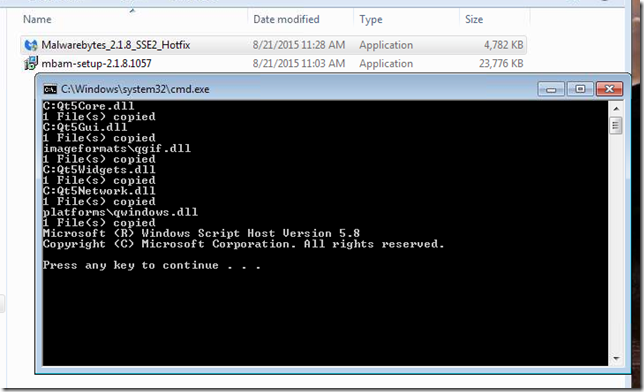
- Download and run the “special installer” file (Malwarebytes_2.1.8_SSE2_Hotfix.exe). This patches/replaces some of the core files causing issue on the older processors.
- Run the Malwarebytes application and it should run normally again.
Step 2 results
Step 3 results.
In another matter, since it had been a while since I had booted this system, my attempts to run Windows Update and download/install the waiting patches was fraught with Update Errors.
After not making much progress on this front, I punted.
I downloaded the WSUS Offline Update utility, built a special Windows 7 x86 update package on one of my other systems. Then (via USB) I copied that client build over to the Shuttle system and ran it a few times. After many restarts I ended up getting the updates on the system without any more errors.
Whew!
For now Windows 7 remains on it, but I am very close now to going to a 32-bit version of The LXLE Desktop Linux distro.
Cheers!
Claus Valca


 CC by 2.0 attribution:
CC by 2.0 attribution: