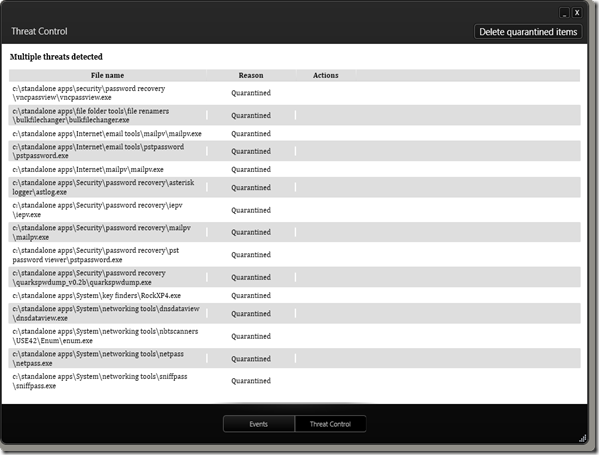
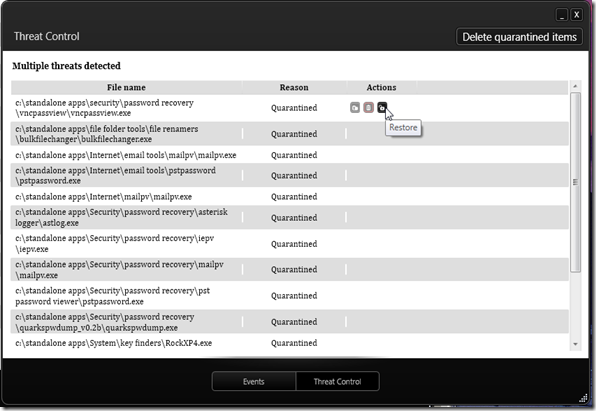
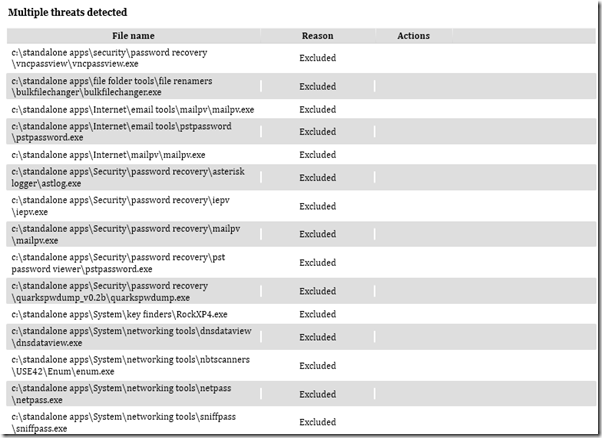
It’s late and has been a super-long weekend.
Lavie isn’t too impressed I’m still sitting at my desk working on posts.
In the meantime, I’m commited to getting this last bit of ForSec linkage collected over the past few weeks out the door so you can have fun reviewing it this week.
Those young and crazy pups over at the Computer & Digital Forensics at Champlain program have clearly caught their dean napping. In an interesting series of posts, they attempt to wreak havoc on different hard-drives and then try to put humpty-dumpty back together again.
MantaRay Forensics - anTech Triage & Analysis System. As far as I can tell, this is the first time I have posted any mention of MantaRay Forensics here at GSD. Spotted in this C&DF@C post Swimming with MantaRay Forensics
MantaRay was designed to automate processing forensic images, directories and individual files with open source tools. With support for numerous image formats, this tool provides a scalable base to utilize open source and custom exploitation tools. MantaRay was developed by two forensic analysts, Doug Koster and Kevin Murphy.
ForGe Forensic test image generator v1.1 - Git Hub project page. from the Overview description:
ForGe is a tool designed to build computer forensic test images. It was done as a MSc project for the University of Westminster. Its main features include:
- Web browser user interface
- Rapid batch image creation (only NTFS supported)
- Possibility to define a scenario including trivial and hidden items on images
- Variance between images. For example, if ForGe was told to put 10-20 picture files to a directory /holiday and create 10 images, all these images would have random pictures pulled from repository.
- Variance in timestamps. Each trivial and hidden file can be timestamped to a specific time. Each scenario is given a time variance parameter in weeks. If this is set to 0, every image receives an identical timeline. If nonzero, a random amount of weeks up to the maximum set is added to each file on each image
- Can modify timestamps to simulate certain disk actions (move, copy, rename, delete)
- Implements several data hiding methods: Alternate data streams, extension change, file deletion, concatenation of files and file slack space.
- New data hiding methods can be easily implemented. Adding a new file system is also documented.
Developer Hannu Visti goes shares a great post over the features and background of this tool over at Forensic Focus. ForGe – Computer Forensic Test Image Generator. This could be a really fresh and innovative tool to help with both simulating forensic images for training and drill purposes. Very interesting and well worth the time to check out. It’s beyond my skill set to review and comment on but if any of the ForSec pros out there have any thoughts or comments, please feel free to drop them in the comments here for our community education.
Linkz 4 Free Infosec and IT Training - Journey Into Incident Response - Corey Harrell goes above and beyond with an outstanding listing of trainings, exercises, and learning resources that are ForSec focused and absolutely-friggin-free for the taking! Corey promises to keep the listing updated so bookmark the page and check back often. I’m particularly interested in the CSIRT-like topics and materials listed like those in the ENISA CERT linkage. I’ve downloaded most all of the PDF versions already to review this week as time allows!
Many of these trainings have supplemental videos and VM’s for download too!
Other specific courses from Corey’s post I’m listing below so I can find them quickly…
- Incident management guide - ENISA CERT
- Tools - ENISA CERT - OMG what a detailed and categorized listing.
- Certified Information Systems Security Professional (CISSP)® Common Body of Knowledge (CBK)® Review - via Open Security Training
- Flow Analysis & Network Hunting - via Open Security Training
- Introduction to Vulnerability Assessment - via Open Security Training
- Introduction to Network Forensics - via Open Security Training
- Offensive, Defensive, and Forensic Techniques for Determining Web User Identity - via Open Security Training
- Utilizing SysInternals Tools for IT Pros course - Microsoft Virtual Academy - Note I think I have already posted this one earlier!
What 'tier 2' & 'tier 3' tools do you load on your forensic workstation(s)? - ForensicKB blog - Lance Mueller has a great list of Tier 2 and Tier 3 apps he considers. I’m pleased to find more than a few in my toolkit already. Note that not all of the software listed here is necessarily free or open-source. More than a few are commercial applications. That’s not at all a bad thing, but just something to be aware of.
Windows Incident Response: Shell Item Artifacts, Reloaded - Harlan Carvey undertakes some very methodical validation exercises on Windows shell item artifacts. Definitely worth reading.
Meanwhile, from another ForSec guy who appears to never sleep… Brett Shavers has been in a posing frenzy over at his Windows Forensic Environment blog site.
Best publicly available testing of WinFE I’ve seen to date - Windows Forensic Environment (Note post info is good but link in it has been superseded by one found in post below.
Updated link on the Mistype project - Windows Forensic Environment
WinFE - direct link to the article mentioned. I agree, it is a truly fascinating read for WinFE aficionados. I’m coming back to read this one carefully this week.
Mini-WinFE - Windows Forensic Environment - This post has tons and tons of screenshots to illustrate the new Mini-WinFE project as well as an introduction that goes over the project features. Very basically, this specific project (1 of 3 promised for alternative WinFE building) allows you to roll your own WinFE boot disk in a “minimal” configuration with FAU utilities, FTK Imager and support for X-Ways Forensics. Total build time is estimated at 10 minutes from start to media in your hand.
Mini-WinFE is out of beta! - Windows Forensic Environment - See you waited too long! The first link was requesting Beta testers. Now it is released! Direct project link here via Reboot.pro and extensive Mini-WinFE project documentation from Misty is linked here.
Quick video on building a Mini-WinFE - Windows Forensic Environment - a very short (3:33 min) YouTube video is available on this post page for those who want to check out the building process.
Since we are on a WinFE bender, let’s shift gears slightly and use that excuse to post a link on the WinFE’s kissable cousin for sysadmins who aren’t quite as focused on disk read-only preservation, WinPE.
How to Customize Windows PE Boot Images to Use in Configuration Manager - Chris Nackers Blog. Chris links to this Microsoft TechNet resource How to Customize Windows PE Boot Images to Use in Configuration Manager
New website and project roadmap - DEFT Linux - Computer Forensics live CD - The DEFT development team has put some fresh paint on their website as well as outlined where they plan to head in the coming months. Congratulations to DEFTA President Stefano Fratepietro and all the community and project contributors who have worked hard to make DEFT Linux a premiere Forensic live CD resource! From that post..
Here follows the forthcoming milestones concerning the new versions of DEFT 8, Virtual Appliance and User Manual.
- DEFT Linux 8.1 with relevant news for Mobile Forensics – November 2013
- DEFT 8 VMware Virtual Appliance – late November 2013
- Roadmap of projects supported by donations – December 2013
- DEFT 8 User Manual – February 2014
- Third Italian National Conference DEFTCON 2014 – Polytechnic of Milano, April 11, 2014
Installing VMware Tools on Kali Linux and Some Debugging Basics - SpiderLabs Anterior - Christophe De La Fuente goes to the mat to show some advanced debugging skills in getting VMware Tools onto Kali Linux. As is pointed out in the comments, there are easier ways to do it, but the experience shared of the road taken makes us all a bit wiser. Which this post then led me to discover and add to my RSS feed pile…
Computer Howto's by Lewis Encarnacion - Lewis’s posts are great. Covering not just Windows 7 topics, but also some of the finer points in using and getting comfortable in Kali Linux.
FAU -version 1.3.0.2464 - Speaking of the Forensic Acquisition Utilities (FAU) it seems a new version came out in August 2013. I don’t think I caught that release. The link has a “what’s new” jump as well as the new binary set download link but for the lazy…from that source:
- Volume_dump and DD now recognize drives with BusTypeSata as devices supporting the ATA feature set. ATA specific attributes are reported for these drives.
- Fixed a problem with the DD --verify option when writing an image to certain to certain drives. Under certain circumstances the DD --verify option reported a spurious failure even though the reimaging of the target drive succeeded and the cryptographic checksum of the destination drive was in fact identical to the cryptographic checksum source image file or drive. This problem did not affect the accuracy of the reimaged drive but required that the user to validate the target drive after the imaging process was complete. Thanks to Suman Beros for reporting this problem.
- When acquiring a physical drive DD now drops the block size down to the device block size when approaching the putative end of the source drive. Hard drives often misreport their capacity either by over estimating or under estimating the true size. The only reliable way to image a hard drive is to attempt to acquire beyond the purported end of the drive and see if valid data is returned. However, we have encountered a few drives that freeze or hang the imaging process if you attempt to read beyond the end of the drive with a block size that is greater than the device block size. Needless to say, this can be disconcerting when you have already read 1 TiB of data only to have the whole process hang on the last few sectors. Dropping down to the device block size when approaching the end of a drive should produce more reliable acquisitions. A disadvantage is that drive acquisition will be slower at the end of the drive.
- Examples have been added to the DD help text which show how to acquire a physical drive.
That’s all for tonight!
Cheers my friends.
Claus Valca