The Valca home is and has been an Amazon Kindle only zone for some time now; thank you very much.
So last year Lavie decided that the E Ink keyboard one (of two) that we had was a bit uncomfortable for her (and not back-lit). She decided to move over to a B&N NOOK Color model. This was in the pre Kindle Fire days so I guess we could tolerate its presence.
The Nook Color served her well enough but when the Kindle Fire came out she had to swing back. It finally arrived last week as a back-ordered Christmas present.
Fortunately, she hadn’t purchased very many books for the Nook so we didn’t deal with trying to see if there were any options for porting her books over to the Kindle. It was an opportunity for a fresh start.
So, she passed her Nook on to her parents a few weeks ago and they loved lot. A lot.
They are on a DSL broadband service, and have a wired XP desktop system. One cable to rule all Internet service. No WiFi except when we stop in for an extended visit and I bring my D-Link DAP-1350 Wireless N pocket router and take over their single network connection for the weekend. Nice but not a permanent WiFi solution.
I suppose we could have just taught them to connect the Nook Color to their desktop via USB and manage it directly but it seemed time to add a WiFi router to their humble network and just do it right.
So that was this Saturday’s “honey-do” and this post is the process we had to go through to upgrade their DSL network and get the hand-me-down Nook color fully transferred over and set up for them.
First Part of the Equation: DSL<-->WiFi
First I picked up a WiFi router. I went with what has become my perennial favorite: DIR-655 Xtreme N Gigabit Router from D-Link
I’ve had this unit personally for a number of years and is rock solid, has both the “N” and older wireless standards, has a rockin-long range, and is super-easy for configuration. The power was important in this case as the location of their DSL modem is on a second floor above-garage room pretty far away from their usual living areas. The signal will carry all the way downstairs and up. Check. And since it is the model I also own and maintain, I know and am comfortable mucking around in the settings. Makes providing extended support much simpler when a problem arises.
Typically I’ve been able to get away with just unbox, connect, run-wizard from CD config, then go and make some manual setting tweaks afterwards. However, this 2-wire DSL modem was a real headache. I could set up the internal network and WiFi perfectly. Just couldn’t get to the Internet through the DSL modem. Plugged the DSL modem Ethernet back to the PC and it was working, reconnect to the DIR-655 and it wouldn’t'.
Long story short, I eventually figured out that for their particular hardware and provider, I had to do a few more custom tricks.
I had to set the Internet Connection Type to PPPoE and enter their DSL username/password. (I got that from their email client settings.) D-Link has a nice Emulator for this router to play around with: D-Link DIR-655 RevB Emulator
Then I had to go into the Network Settings and change the router IP Address to use 192.168.1.1 from the default IP address of 192.168.0.1 Turns out that the default IP address was conflicting with the internal Ethernet-facing IP address provided by the DSL router. This was the real trick.
Once I got the network stabilized, I tested the configuration survivability by powering off both the DSL modem and the D-Link (to simulate a power-failure), then powered them back and and made sure the PC could get to the Internet. Check.
This one was actually a DIR-655 RevB model so I then saved my configuration file, downloaded the latest firmware and ran an upgrade. Success. Naturally it lost all of my settings, so I had to upload my saved config file and it was back to normal. Yea me!
More helpful notes I had to find to work out that issue:
- DIR-655 & ATT DSL - D-Link Forum
- [Solved] Dir 655 problems - Setup-Configuration-Security - Wireless-Networking
- 3.15 D-Link Info AT&T Southeast Forum FAQ - DSLReports.com, ISP Information
So now I had taken care of the DSL<-->WiFi router part of the equation. Next the Nook.
Second Part of the Equation: Nook<-->In-Laws
This actually was almost harder than getting the router added.
Because the Nook was a hand-me-down, Lavie had it configured with our WiFi settings, her name, and the account information. She said she didn’t mind if her parents just kept it that way and we just change the billing information on the account. However, she had followed bad password security and used the same information she has used on several other of her on-line accounts. I needed to break that clean.
The rub was that Lavie had already purchased some books for her dad under her Nook account and I didn’t want to loose them. What I wanted to do was to figure out if/how I could transfer the B&N account she had set up over to them and remove Lavie’s information and add-in theirs.
Here’s what I had to figure out doing to keep the original Nook account (and purchased items) but swing it fully over to the in-laws “clean”. Note this was a serious trial-n-error process that took almost two-hours longer than it should have (by my reasoning). This is the “clean” version and from what I later read on the web, seems to be the only way currently I know of to “transfer” a nook from one email/owner to another one while preserving the purchased items.
Note: Lavie didn’t have any files or items on her Nook that were not already associated in her Nook account (like manually installed music/videos/pictures/stuff) so I didn’t have to deal with the loss of those in this process. If you have those on your nook and want to preserve them, you probably want to off-load/copy them to your PC first before beginning this process. Again, this assumes everything you want to keep is safe and and associated in the B&N account you will be restoring from. YMMV. So you were cautioned, so you were warned.
- Take your Nook (the one you want to change the owner name/email account info on) and go into the settings and find the option to Unregister/Erase your Nook. Do this first. Really. BEFORE you do ANYTHING ELSE. It sounds serious and I guess it is, but that’s how the Nook rolls.
- Once your Nook is reset, log into your B&N account from the BN.com page. If you can find the login link on the page. Seriously. I was using Chrome and it took me ten minutes to realize that tiny gray bar (which perfectly matches the address bar gradient and bookmark text in Chrome at the very top of the page) with the tiny text is the login location. Sheesh. Hey B&N. Can you make it a bit more obvious please?
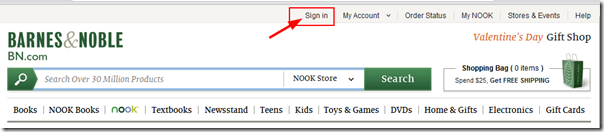
- Now change your name in the account. I changed it over from Lavie’s name to the in-law’s.
- Change to your new email address in the account. Changed from Lavie’s to the in-law’s.
- Change the password if you desire…I did so desire and changed to a complex full 15-character (most allowed by B&N) password.
- Change the Shipping/Billing addresses as needed. Now set to the in-law’s.
- Change your secret challenge question if needed. Selected and changed as picked by the in-law.
- Update the associated credit card information. Definitely the in-law’s here!
- Etc.
- Once all the account information is updated to the way you want it and saved, make sure you can successfully log-in/out of the account. Good? Great.
- Next fire up the now reset Nook and go through the setup process from scratch.
- Accept the Terms of Service.
- Set the Time Zone.
- Connect to a WiFi network. It found the WiFi network I had earlier got working, I fed it the secure passphrase and it connected perfectly and strongly.
- Register the Nook. (I passed it the updated email address from above and the new password.)
- It Registered and identified perfectly as the in-law’s nook now.
- Yea me!
- We went to the Library and told it to refresh and all the books previously associated with the account flowed back down and “installed” without any issue.
- I then went to the applications and downloaded the waiting previously purchased/associated apps. Perfect!
- The Nook was now fully theirs.
Equation Solved: DSL<-->WiFi<-->Nook<-->In-Laws
We spent another hour or so going though the list of free NOOK Books at Barnes & Noble. We found a good selection of mystery and history classics to keep them both occupied for the next couple of months. Pop also found a good old-west history book to purchase as well. It was good training process and confirmed the purchase/credit-card association with the account worked.
Mission accomplished, five hours (and one super-awesome BBQ baked-potato for lunch) later, the equation was solutioned.
Additional Notes:
- Daughter hovering over your shoulder on the back of the couch while you have your laptop and the Nook balanced on your lap troubleshooting. Like a vulture lurking. Not helpful.
- Daughter making organic microwave popcorn and snuggling up munching away while you have your laptop and the Nook balanced on your lap troubleshooting. Also not helpful.
- Daughter not asking once to borrow your laptop to check out the WiFi and Facebook while you are troubleshooting. Very helpful and appreciated.
- Sense of patience and humor from all participants; self, daughter, in-laws. Very helpful.
- Extended road-trip to in-laws up and back with daughter on beautifully clear and cool day through the east-Texas pines lined country roads. Priceless.
Final thoughts.
Lavie had successfully set up her Kindle Fire just fine by herself (thank-you-very-much) so I didn’t get to participate in that except for applying a smokin-hot DecalGirl skin she had picked out for her Kindle (my hands are super-steady for such things). She had also picked up screen protector but turns out that it is a full edge-to-edge cover which would cause issues with the DecalGirl skin on the front (which frames the blacked-out display edge portion). I suggested trimming it down so it fits inside the DecalGirl border but she passed on that for now…so it remains uninstalled at the moment.
Alvis and I both have the WiFi-only version of the E Ink Kindle model and we love them. Light, super-durable, and the charge lasts a long time.
Last night Lavie did ask me to copy some songs from her iTunes playlist to the Kindle Color. You can do it a few ways, apparently most popular is to upload music from your PC/Laptop to the Amazon Cloud Player service. What I ended up doing was to connect Lavie’s Kindle Fire directly to my PC (which holds our iTunes library) via USB, then opened iTunes, opened her play-list, sorted it by album, then I selected a song, hit the three key-combo “Ctrl-Shift-R” which opened up the location of the file itself on the library, selected any additional songs in her playlist from that album, copied, then pasted them in the Music folder on her Fire. Repeat as needed. It was a bit slower but got the job done. All of them appeared to be in the compatible .m4a format and I didn’t find any .m4p that would not have been supported.
She was jammin…though I left her to work out creating a new playlist from those songs directly from within the Kindle itself.
Adding photos/videos would be the same process, locate on your PC, drag/drop into the correct folder on the Kindle when it is attached via USB and shows as an external storage device. Piece-o-cake.
Based on the (admittedly still limited) time I spent on both the Nook Color and the Kindle Fire, I found the Kindle Fire was more to my liking. I could navigate around the Nook Color and it was pretty intuitive (never did get around to reading any manuals on either one) but I did like the “hand-feel” of the Kindle Fire better. And the navigation just subjectively felt better to me on the Kindle Fire than the Nook.
Since I am (for now) a hard-core Kindle E Ink format lover, the extra bells-n-whistles of the Kindle Fire haven’t captured my eye yet, so I cannot comment on app-support and performance of videos/games/applications between the Nook Color and Kindle Fire.
The other think I noticed while helping set up the in-law’s Nook was the apparent lack of easily found free E Books directly within the B&N Nook store. Searching for E-books at B&N was a super-pain as well. In the end I had to do a Google Search to find this “all-in-one-place” location for Free NOOK Books.
When I first got my Kindle, right on the Amazon Kindle pages I found this Amazon.com: Free Book Collections: Kindle Store link. In no time flat I had downloaded almost twenty amazingly awesome classics from literature, philosophy, religion, and reference. All free. I’ve since moved on and expanded my collection to include many additional eBooks I’ve found scattered on the net including some great ones in PDF formats and I have made a number of eBook purchases for the Kindle as well. That smooth and awesome experience jumping into the Kindle right-out-of-the-box probably helped solidify my personal leanings towards the Kindle platform. I’m sure there are lots of additional Nook-compatible ebook formats and ways you can get them to your Nook, but for the in-laws, having in-store access to locate and select-to-download-direct to their Nook has a lot of appeal.
I’ve got a lot of great Kindle resource links saved and building for a GSD Kindle post…along with some cool technical and for/sec bits related to the device I have found as well. Hopefully that will come soon.
Anyway, hope this helps someone else trying to get their DSL <-->WiFi<-->Nook<-->In-Laws equation to balance out and solution properly. Now I remember why I found Calculus so challenging. It was a real love/hate relationship and this turned out to be very much the same.
Cheers!
--Claus V.

 I can’t believe I’ve been blogging now (fairly) consistently since 2005. I’ve gone from a peak posting rate of 311 posts in 2007 down to a low of just 40 posts last year in 2011.
I can’t believe I’ve been blogging now (fairly) consistently since 2005. I’ve gone from a peak posting rate of 311 posts in 2007 down to a low of just 40 posts last year in 2011. Last week I found a cheap trestle-style mini-desk that was perfect in color, style and size for the living room. With minimal rearrangement I was able to place it in the living room along with a nice matching traditional wooden chair with a faux-leather seat cushion. It was a great pairing. While not my favorite in terms of style, it was a perfect pairing of form and function (and price) so I struck while the iron was still hot.
Last week I found a cheap trestle-style mini-desk that was perfect in color, style and size for the living room. With minimal rearrangement I was able to place it in the living room along with a nice matching traditional wooden chair with a faux-leather seat cushion. It was a great pairing. While not my favorite in terms of style, it was a perfect pairing of form and function (and price) so I struck while the iron was still hot.