cc image credit image by Fernando de Sousa on flickr
Happy Father’s Day!
Here is a real varied collection of links. Enjoy!
Security Solids
- Java 7u5 and 6u33 released - ISC Diary - Make sure you get your Java updates on. Despite all attempts, my Java app still doesn’t want to notify me updates are available (at home) so I keep a constant eye out for update notices and install them myself.
- Oracle Java Runtime Environment 7 Downloads - Oracle - Here’s one place to get them direct from source.
- Inside Flash Player Protected Mode for Firefox -Adobe Secure Software Engineering Team (ASSET) Blog - Adobe Flash Player also got updated, particularly impactful for Firefox users (see next tie-in grouping below). YMMV. You can get the very latest version for different platforms here at this Adobe - Web Players link. Or hop over to Major Geeks.
- (IN)SECURE Magazine - Issue #34 is now out in PDF format.
- How LogMeIn is enabling scammers to profit - Troy Hunt’s blog - Troy continues his ongoing battle against fake tech-help scams. This time he examines how “LogMeIn” could do more to help prevent their great service from being leveraged for The 3vil, if they chose to.
- Free cruise phone scam masquerades as political survey - ESET ThreatBlog - I’ve started to periodically get a few calls now on our cellulars from unknown numbers…they follow a pattern of tracing back to a cruise-operation. If it isn’t a number already in my contacts, I just don’t answer and if critical, the caller will leave a voicemail and I will call back immediately. If not…too-bad-do-dad! So it was with interest I read this ESET post by Aryeh Goretsky and how an end-run may be going on around cellular do-not-call list participation.
- Close Call with a Caribbean Cruise Line Scam - IT Secure Site - More on the above.
- 'State-sponsored attackers' using IE zero-day to hijack GMail accounts - ZDNet’s Zero Day blog. I’ve seen the notice of “state sponsored attackers” recently and was wondering “what’s up with that?”. Now I know. more details at this Google Blog post: Security warnings for suspected state-sponsored attacks. Chron.com TechBlog’s Dwight Silverman has some advice and links to a Microsoft “hotfix” for the issue: Bad guys using unpatched Internet Explorer flaw to hack Gmail accounts.
Firefox Paisleys
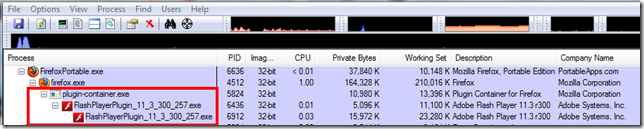
In my last GSD post, I touched a bit on some issues I was having with Firefox 13 and Flash. My issues may or may not have been related to these, however there are some serious headaches for Firefox 13 and Flash users.
- Firefox 13 tripped up by Flash patch - Update - The H Security: News and Features
- Inside Flash Player Protected Mode for Firefox - Adobe Secure Software Engineering Team (ASSET) Blog
- Flash 11.3 doesn't load video in Firefox - Firefox Help
- Flash 11.3 Video Issues In Firefox - Firefox Extension Guru's Blog
- Firefox 13.0 Release Notes - Mozilla Desktop
- Firefox 13.0.1 Released -Firefox Extension Guru's Blog. The Guru helpfully points out the following:
”Note: In regards to the Flash Bug (747683) this does NOT address issues related to Flash videos not playing in Firefox (which may also be affecting Firefox 12.0.x users as well) for Windows Vista and 7 users. “
- Wallpaper your Firefox new tab page - Mozilla Links. However all is not lost, you Firefox freakers can tweak your “new tab page” to display a wallpaper background image if desired.
Sysadmin Stripes
- Malware Hunting with the Sysinternals Tools - TechEd North America 2012 \ Channel 9 - A new presentation video from Mark Russinovich on using Sysinternals Tools to do some malware thumpin! Watch streaming or pick from one of two formats for direct downloading and viewing later. This presentation includes real-case reviews as well as a live analysis of a Stuxnet infection. Sweet!
- Windows Exploratory Surgery with Process Hacker - SANS Windows Security Blog - Jason Fossen shares PDF version of his presentation primarily using the freeware tool "Process Hacker”. It is a really great review of the different angles one can take with a limited tool-set.
That got me thinking a bit. Process Hacker has matured quite a lot since I last downloaded a copy and the new one certainly has more polish on it. I went through my utility pile and offer below some other great freeware utility process-monitoring tools you may be interested in visiting again.- Process Explorer - Sysinternals - One ring to rule them all. Still the very first utility I place on my Windows systems and swap out the default Task-Manager with. It continues to be upgraded so if you haven’t got the latest version for a while, you are missing out!
- System Explorer - This one also has grown up quite a bit from my last download a few years ago. I like the tabbed interface. The “Performance View” tab is very neat. Process Explorer’s graphs are still a bit more detailed looking but it doesn’t provide an all-in-one dashboard view like System Explorer offers.
- Daphne - Not as GUI pretty as the others, but what it lacks in pretty it more than makes up in back-to-basics tightness.
- Process Viewer for Windows - This project hasn’t been updated in a while but again, the “latest” update was still fresher than the one I’ve been carrying around for quite a while. This one is a bit more feature basic. If you aren’t ready for the power of some of these other process utility tools, but need more detail than the default Windows Task Manager (at least in XP) then this may be a friendly choice.
- ProcessActivityView and ProcessThreadsView - These two application from NirSoft compliment each other nicely.
- NoVirusThanks EXE Radar Pro - Provides process monitoring and alerting as well as to kill processes on demand.
- ESET SysInspector - This is a complex, single-file-executable. It provides detailed information on running processes as well heuristics reporting on items found. I find it particularly helpful in assessing a system. It may not tell me exactly what is going on, but it often will help be refine my focus a bit.
- WHITEPAPER: Windows PowerShell 3.0 and Server Manager Quick Reference Guides - Kurt Shintaku's Blog
I learned this week about a “honeypot” project that attempts to capture USB-seeking virus/malware by creating a virtual USB-drive honeypot. This is a cool project and I hope it continues to see success in development.
- Catching worms with ghost flash drives - The H Security: News and Features
- HPSoC Project 1 - Ghost USB Honeypot -The Honeynet Project
- ghost-usb-honeypot - A honeypot for USB malware - Google Project Hosting
- Ghost USB honeypot released - Help Net Security blog
More interesting tips for admins…
- Microsoft .NET Framework Repair Tool Download - Microsoft Downloads
- Windows 8 – Script for customizing WinPE 4.0 – Part 2 – Customizing the Wallpaper - Anything about IT
- Local admin accounts vs. the default Administrator account - Windows Networking
- Where is That Group Policy Setting? - Windows Networking
- Active Directory Replication Status Tool - Bink.nu
- Download: ADREPLSTATUS - Microsoft Download Center
- Video: User Rights - Server vs Domain Controller - Windows Networking
- INFO: Why the heck is my Outlook .OST so big? - Kurt Shintaku's Blog
Network Knitted
- ARP Scans - A Ping Alternative - LoveMyTool blog video presentation by Tony Fortunato.What’s really going on the wire with Colasoft MAC Scanner Free.
- Script to resolve hostnames to IP address - Computer Security Forum. Recently I was presented with a massive list of Hostnames for PC’s on our network. The assignment was quite simple, provide the associated IP addresses. No problem, I could manually ping each one by hostname, copy the result (if alive) and paste into my spreadsheet. Well, no. I wanted to go home to my family that night. Instead I found and ran this nice simple script against a cleaned up text-file of the Hostnames. My success ratio for IP grabs was over 90%. The other 10% required some manual followup (systems turned off, shelved, etc.) but it made quick work. I wasn’t able to find a good free GUI-based alternative, but this did the job wonderfully.
- Extracting DNS queries - NETRESEC Blog - Either by Tshark or NetworkMiner.
Utility Dotted
- NTFSLinksView - View NTFS symbolic links and junction points - NirSoft utility update
- Backup Windows User Profile Folders & Web Browser Profiles - Auslogics BitReplica - AddictiveTips review and walkthough for a new profile backup utility.
- Backup for Windows 8 & Co: BitReplica - (Google Translated from German) - Caschys Blog
- BitReplica - A free tool for backing up files stored on your Windows PC
- Batch-Rename Files In Windows Using 8 Different Presets - AddictiveTips reviews the PDFN
Batch File Rename Utility.
- Spreadsheet Compare - The Fool on the Hill - Neat little Microsoft Excel Add-in to compare and highlight two spreadsheets. As seen in this review How to Compare Previous Version of Excel Spreadsheet– A Diff for Spreadsheet over at Windows7hacker.
- VMware closes holes in its virtualisation products - The H Security: News and Features
- New VMware Workstation 8.0.4 and Player 4.0.4 - (Google Translated from German) - Born and Windows IT Blog. What I found interesting is Gunter’s catch of the EULA details that allow VMware to collect and use info about your use of software including IP address, hardware ID, OS information and other “non-personally identifiable” usage stats. Also that by accepting the EULA and using the software you agree to a two-year post termination of software use agreement for folks to audit your books, records and computing devices to determine your compliance with the EULA and payment of license and support service fees. I’m sure this is pretty standard stuff and proper use of the free software they make available shouldn’t concern the average user, but it is another reminder of what lives in the EULA’s. Just be aware.
- VMware Player: Run Windows 7, Chrome OS - Free Download for a Virtual PC - VMware
- Download VMware Player 4.0.4 - FileHippo.com - alternative download link
Foresensically Checked
- New Plugin – “TypedURLsTime RegRipper Plugin” - RegRipper
- Digital Forensics Stream: TypedURLsTime RegRipper Plugin - Digital Forensics Stream blog
- RegRipper Supplemental Plugins Updated (regripperplugins_20120528.zip) - RegRipper
- DEFT Pen ready for download DEFT Linux - 2GB and 4GB versions of DEFT “LiveCD” 7.x to load onto a USB pen-drive rather than the optical media version.
- WinPentest v1.3.0 - woanware - Major updates.
- Compromise Root Cause Analysis Model - Corey Harrell wonderfully thought-provoking post on DFIR concepts over at his Journey into Incident Response blog. There will be a pop-test after the review…
- Am I pwn3d? Windows *Non-Native* Tool Triage is a follow-up post to the Am I pwn3d? Windows *Native* Tool Triage on using “simple” tools to perform system triage. Posted on Foundstone’s Open Security Research blog.
- Red Rock Solutions - RRTX Blog: ShadowKit - Red Rock Solutions RRTX blog - Neat and easy-to-use tool for recovery of Windows Volume Shadow Copy files. I’ve got several tools like this, and having a few makes it easier for me to find the one that helps me best in a particular event.
- Windows 8 Forensic - File History - Random Thoughts of Forensics blog brief post with some backing linkage.
- Timeline Analysis and Timeline Analysis, and Program Execution - Two excellent posts over at Windows Incident Response blog.
- Prefetch Hash Calculator + a hash lookup table xp/vista/w7/w2k3/w2k8 - Hexacorn blog utility/technique.
Cheers!
--Claus V.