I really need to be blogging a Linkfest past 11 PM on a Sunday night.
I’ll be getting up at 5 AM. I’d do the math but I don’t think it is going to work out in my favor.
I had expected to do a lot more blogging this weekend that I ended up producing.
See…I spent a majority of Saturday swapping out our wired D-Link router with a spanking new D-Link wireless router.
Yeah, during the setup process I ended up blue-screening our Vista notebook, spent hours of extra time troubleshooting the other laptop’s hardware, BIOS, and OEM software, and black-screen-reboot looped our XP desktop system.
Not bad for a day’s work.
Yes I got all three of them working again. No, I didn’t get the monster causing the havoc and pandemonium fully resolved. That’s pending a tech-call to D-Link, per their request.
Yes the wireless is working awesome on both laptops, as are the wired connections.
All-in-all it was quite a learning experience. Still have some more lock-down overkill configurations to go through but I’ve done enough at the moment to feel pretty secure in my efforts.
And yes, there will be an eventual post about this experience.
That’s my excuse at least.
Hang on, these are going to come at you pretty fast…just like that wireless connection now!
Here's your big plate of Linkfest!
Got your fork ready?
The Big Picture - Boston.com – Really awesome photographic essays from Boston’s on-line newspaper presence. I really like the space and nature photography, although the photo-journalistic stories are captivating as well. While I haven’t added this to my RSS feed list, I have bookmarked it in my “must view weekly” folder.
SDN Program News : weblog – Java SE 6u10 has been released to the public in final form. I’d say this needs a whole other post of its own. Suffice it to say, stop and go get it right now. download Java SE 6 Update 10. See also: Special Event: Java SE 6u10 Release : The Planetarium. BTW, The Planetarium seems to be a company blog hosting news about all things Java. Might be interesting enough as a source of leads of Java-related info.
Confessions of a freeware junkie: Export/Import your drivers [update]: DriverMax - great review showing some major changes to the freeware driver backup tool DriverMax. This one got a major update and has some new features to go on-line to search out the hardest to find system drivers. No guarantee it will get everything but definitely worth looking into if your drivers are hard to come-by. See this previous GSD post Backing up Windows System Drivers on why this might be a Good Thing to look into.
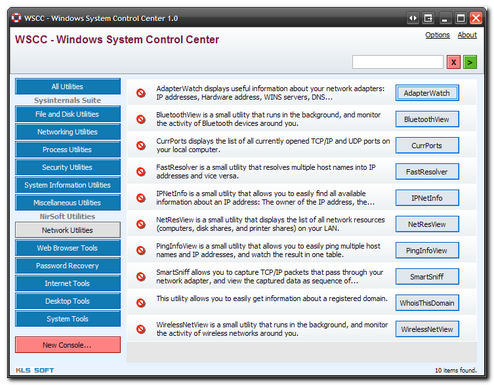
I finally dug up NirBlog. This is Nir Sofer's NirSoft blog. What makes this so valuable to me is that now I get to see some of the thought and consideration that goes into making these fabulous tools. For example NirBlog: New utilities are coming soon points out several new goodies just over the horizon. Most exciting to me is the UserProfilesView: "This utility displays the list of all user profiles that you currently have in your system. For each user profile, the following information is displayed: Domain\User Name, Profile Path, Last Load Time, Registry File Size, User SID, and more." Not sure how helpful this would be to hard-core forensic experts, but to the average sysadmin supporting a desktop in the field, this could be some golden info to have at hand. Also worth reading is NirBlog: Current AVG False Positives. I'm so frustrated at work that my system gets pegged on the top of the A/V list logs since the Symantec AV always squeals about the "hack-tools" utilities that involve key-finders, password finders, and asterisk revealers. All of these are legitimate tools I must use from time to time in my desktop and system support capacity. However due to the backlash the AV systems give, I have to keep them on a standalone USB stick, with write locked (to prevent A/V deletion) and only use them on demand. Grrrr. I feel Nir's pain and frustration. Other improved apps this week from NirSoft are PasswordFox and ShellExView. So go and add NirBlog to your RSS feeds. You will be glad you did!
PortableApps.com AppCompactor - I don't really ever use an app-compactor utility. Basically what they do is to re-pack executable files to make them smaller in size. With USB drives getting bigger by the season and prices falling faster than the price of oil of late, I don't really have a need to make them smaller. Some folks swear that it makes these programs perform faster on slower USB devices. I don't know. I do know that some A/V programs tend to have a higher false-positive alert rate on repacked legit apps as this is a somewhat common technique for some malware writers to use as well.
Frets on Fire Portable - PortableApps.com - I've never really gotten into the whole "Guitar Hero" thing, but Alvis is impressed by it and in the hands of a skilled gamer, it is a sight to behold. Naturally I had to take a look at this freeware version and it is impressive. It's fairly faithful to the concept and the delivery is spot on. In the words of the tutorial master, I do suck at this game, but it was fun trying! I might even come back to it. The game comes with just a handful of tunes, but if you pop over to Frets on Fire Wiki Songs and register (free) you can download what look likes a whole mass of awesome community crafted songs to add-in. For more info check out the official Frets on Fire Portable homepage. Rock-on!
Universal Extractor got a seriously major update this past week. This gem is my secret weapon to avoiding installing much of the software I use. It will have to rate a post of its own later. Suffice it to say, if you work with or deal with compressed files or installer packages, you must have this freeware gem on your system somewhere. It's more useful than a can-opener in a post-hurricane kitchen drawer. See this change log hosted over at FileHippo for a full breakdown of what you are looking at with your update.
muCommander: a cross-platform file manager - never heard of this one, and I have blogged about a few goodies in file managers before. This one is neat in that it is truly multi-platform in MacOS X, Linux, Windows, Debian, and even a Java application version. Take your pick. It was pretty nice and seemed to work well.
Stupid Chrome Tasks - clever little app written by a coder frustrated with a few but important missing elements in Chrome; namely the ability to clear the download history out of the browser and the second, and likely more important, the ability to export your Chrome bookmarks out of the browser and into an HTML file that other "modern" browsers can all import. I guess Chrome developers figured it was so great no one would think of going back, thus they wouldn't need to export their bookmarks any more. Reminds me of something a college history professor said once, "Hubris, it will get 'em every time!" Spotted over at Lifehacker.
RepairIE is a great program tweaking tool to help you muck up your Windows system and leave it a quivering mass of blue gelatin. No, wait. If you don't know what you are doing with this tool it will quickly leave your system a quivering mass of blue gelatin. That's more like it. Really it is just an GUI interface to a bunch of important and useful registry hacks. Good stuff! Spotted over at Download Squad. See also the related Nawras PC Supervisor application which also provides a GUI interface to a bunch of tweaks.
VisioCafe - If you use Visio, then you will want to bookmark and investigate the great free template files here. Lots of pc, network, and related objects.
GoToMyPC : Install Software - Only leaving this link here so I can find it easily. Been installing a ton of this software last week and never could remember where I direct-downloaded the setup file from. Now I've got it and bookmarked to boot!
Vector Magic | Precision Bitmap to Vector Conversion Online - Blogged this one before as well. Kinda related to the Visio work mentioned above. Vector images scale in Visio so much better than any other graphic format. However, it can be a challenge to reformat them to look nice. Vector Magic lets you upload your image files for free and then vectorizes them in a PNG format. Works very, very good. Highly recommended.
Then, when you have your PNG vector file, process it one more time with PNGGauntlet - PNG Compression Software This is a great (and tiny) little application that does some kind of magic mojo dance to get your PNG files shrunk down and optimized a bit more. All I can say is that it worked wonders with the ones that I got back from Vector Magic. The files processed with no issues and the size was much smaller when done than before. Good stuff.
Finally, I had the need to download and use the previously mentioned freeware tool Microsoft Research Image Composite Editor (ICE) which stitches several related digital images into a panoramic-style single image. It worked perfectly and did such a great job, the digital photo expert of our crew was so impressed with the tip, demonstration and results, I got a free lunch out of it. Not bad!
Cheers!
--Claus