OK, in the grand scheme of World Events, getting the latest Xplico release to update/install in the latest Ubuntu LTS release isn’t that critical.
But it does get frustrating when something so easily-difficult turns into being something a case of something so difficultly-easy to solution.
Submitted for your entertainment and education, upgrading both Ubuntu 14.04 LTS and Xplico 1.1.0.
I’ve covered more than a few guides now here at GSD on getting Ubuntu upgraded in my VirtualBox session. Each time it goes a bit more smoothly than the last.
- Ubuntu 12.10 (Quantal Quetzal) Upgrade - grand stream dreams blog (10-2012)
- Ubuntu 13.04 (Raring Ringtail) Upgrade..a bit faster this time - grand stream dreams blog (04-2013)
- Ubuntu 13.10 Upgrade - Lessons Learned & VIDMA utility found - grand stream dreams blog (11-2013)
Likewise, getting Xplico installed the very first time on my own (rather than using it in a pre-bundled virutal machine appliance or LiveCD distro) was quite the effort.
- Self-Installing Xplico in Ubuntu - Virtual Edition - grand stream dreams blog (03-2011)
Fortunately, after contacting the wonderful team at Xplico, they added some super-easy “scripts” to their wiki page to make the process a breeze for Ubuntu builds up though 13.10.
So what could go wrong this time?
Apparently still quite a lot.
First, let’s cover the Ubuntu upgrade using the well-worn GSD process.
Here you go…documented for your entertainment and my education.
- Find in RSS feeds that my Ubuntu 13.04 Raring Ringtail install has a Ubuntu 14.04 LTS Trusty Tahr update available.
● Ubuntu 14.04 review: Missing the boat on big changes - Ars Technica
● Ubuntu 14.04 "Trusty Tahr" Brings Small Changes, Long-Term Support - Lifehacker
● Ubuntu 14.04 LTS is here -- Linux fans, download it now! - Betanews
● Ubuntu 14.04 review: Trusty Tahr adds finesse and choices to the Ubuntu desktop - Desktop Linux Reviews
● TrustyTahr/ReleaseNotes - Ubuntu Wiki - Made sure my Oracle VM VirtualBox platform I run it is is current. Upgrade accordingly first.
- Excitedly start the in-place upgrade of my VirtualBox Ubuntu build.
- Play it safe to prevent VirtualBox upgrades messing with Ubuntu by first disabling 3D acceleration in the VM machine settings.
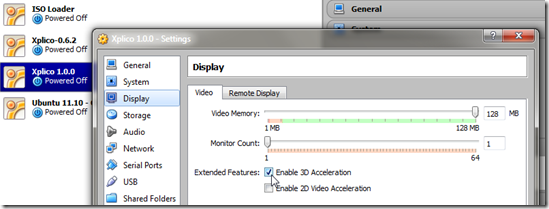
Then install/upgraded to the latest VirtualBox Extension pack within Ubuntu proper. Unlike last time I knew what the correct option clicks to get the Extension pack installer auto-running after I mounted the CD/ISO file.- First, run the installer from the host.
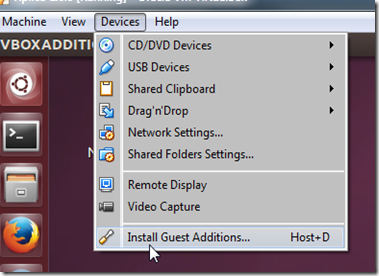
- Next choose the “Ask what to do” option.
- Run the auto installer
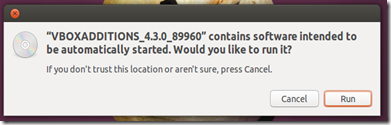
- Authenticate and install
● How do I install Guest Additions in VirtualBox? - Ask Ubuntu.
● Installing Guest Additions on Ubuntu - VirtualBoxes
- First, run the installer from the host.
- Once done, I rebooted the system after re-enabling the 3D Acceleration option in the VM settings.
- From there I continue my previous successes by using Daniel Benny Simanjuntak’s tip in a previous Ubuntu post comments to run the following command from the terminal to start the upgrade process.
…through terminal one can upgrade as well using the command:
sudo do-release-upgrade -d - For an alternative method found check out this Upgrade Ubuntu 13.10 (Saucy Salamander) to Ubuntu 14.04 (Trusty Tahr) via Tecmint.com post.
- Let it run for a while…do a few reboots…looks like a Flash package is causing some non-fatal errors…moving on anyway…
- When it is all settled down, I log in and kick the tires a bit, and change the desktop to the more dramatic “Sea Fury” image from the pickings offered.
- Looked for and updated any pending applications needing updating. Done.
- Check “Upgrade to Trusty Tahr” off my to-do list.
So far so good.
Second, let’s cover getting Xplico working again.
So despite some fairly recent updates with Xplico - Open Source Network Forensic Analysis Tool (NFAT) having come out, for my simple purposes, I’ve been running the Xplico 1.0.0 version up to this point in my previous Ubuntu builds.
As previously mentioned, the Xplico development team (specifically the most gracious and patient Gianluca Costa) kindly corresponded with me after I asked some follow-up questions to my Self-Installing Xplico in Ubuntu post. That eventually helped lead in a small way to:
- Xplico 1.0.0 Released - with notice of the new Xplico Repository and
- the fantastically helpful ubuntu page in the Xplico Wiki giving you the following install options from:
- The Xplico Repository (currently for Ubuntu 11.04 through 13.10)
- SourceForge for both Ubuntu 12.04 and Ubuntu 11.04 & 11.10)
Knowing that the Xplico team had recently released Xplico 1.1.0 in late December with some nice feature enhancements, I thought it was finally time to do the upgrade.
First, I launched Xplico 1.0.0 from within my Trusty Tahr machine…and it completely and totally failed to work.
Might have something to do with all that “Apache” stuff I noticed going on during the upgrade to 14.04 LTS perhaps?
No problem…I’ll just go back and reinstall the older Xplico 1.0.0 version using any of those handy Xplico “scripts” on the Wiki page.
Fail.
My first attempt was to use the first installation method from the Xplico repository.
That seemed to “mostly” work except it didn’t really work cause embedded in all the Terminal output were these potential issues:
Err http://repo.xplico.org trusty/main i386 Packages
404 Not Found
and
W: Failed to fetch http://repo.xplico.org/dists/trusty/main/binary-i386/Packages 404 Not Found
E: Some index files failed to download. They have been ignored, or old ones used instead.
Yep…not going to work or continue with the build process with those buggers.
OK, lets move on to the SourceForge package source/method.
Snap, same errors…
Well, granted, I may have been rushing things out the door, maybe waiting a few days would help and the repositories could just happen to be off line.
So I came back a few days later (OK, just this morning) and tried again netting the same results.
So, being a somewhat clever and resourceful person, I did what most folks wouldn’t dare think about doing to fix a technical problem in a area (Ubuntu) they don’t know enough about; I fired up the email and asked for help from the most gracious and patient Gianluca Costa. Funny thing is his email to me back from January 2012 is still sitting in my Inbox, one of about 8 emails I keep there for quick reference or encouragement. I knew there was a reason for that.
Less than 30 minutes later, from across the globe, came a wonderfully helpful response with the following critical bits amongst some other nice content:
If you like to test the 14.04 packages, their links are:
http://projects.xplico.org/xplico_1.1.0-14.04_amd64.deb
http://projects.xplico.org/xplico_1.1.0-14.04_i386.deb
After checking with him first, Gianluca kindly allowed me permission to share that information with you. Please do note these are still a work in progress and some fine-tuning might occur before their “public” release which should happen very soon...but if you are struggling for Xplico 1.1.0 to get working and just can’t wait, there you go.
Probably for a seasoned Ubuntu professional, that would be all the information needed to get Xplico going again…alas…not so much for me; at first.
Here’s how I finally got it going about an hour after getting the package repository links.
Now to be clear and fair, I did need to make some fresh coffee during the process. So it didn’t really take me an hour total! But then again in more honesty, I made the fresh coffee using a K-cup machine Mom and little Bro gifted me for house-sitting…so the coffee making process didn’t take as long as one might think. Seriously…just a few minutes. Cheese-and-crackers! …now that explanation seems to make it look like it did take me closer to an hour…umm maybe I slowed down to savor that rich Italian roast blend I had to honor Gianluca for his reply?
Moving on…
- In Ubuntu, I opened up Firefox and downloaded the “xplico_1.1.0-14.04_i386.deb” package to my downloads folder.
- I then right-clicked the package and selected Open With the “GDebi Package Installer” as that seemed as cool a thing to do as either of the options offered.
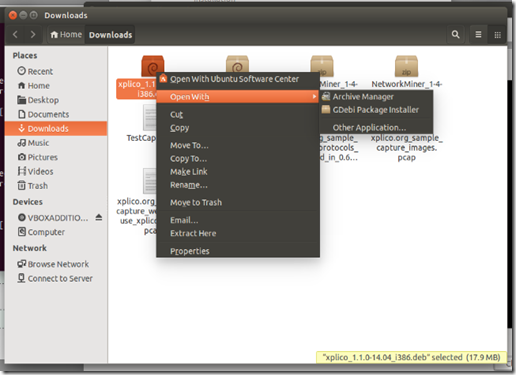
- It needed some prompts answered, but it ran OK until near the end when I got this:
![oclyluha.buq[5] oclyluha.buq[5]](http://lh5.ggpht.com/-gJZtYfq1B0o/U1w8PaN3CII/AAAAAAAABp0/OGG--YXQ0q4/oclyluha.buq%25255B5%25255D%25255B4%25255D.png?imgmax=800)
- That did NOT look promising…but I can follow instructions like a few people can
- I opened a fresh Terminal window and ran “sudo apt-get install -f”
- That did a bunch more things. I’ve saved the text output to place with Alvis’s early macaroni art pictures from kindergarten class but here are the highpoints (yes…I’m leaving some things out for brevity…like that matters at this point in the blog post):
The following packages were automatically installed and are no longer required:
libquvi-scripts libquvi7
Use 'apt-get autoremove' to remove them.
The following extra packages will be installed:
apache2 libapache2-mod-php5 libpq5 python3-psycopg2
Suggested packages:
apache2-doc apache2-suexec-pristine apache2-suexec-custom php-pear
python-psycopg2-doc
The following NEW packages will be installed:
apache2 libapache2-mod-php5 libpq5 python3-psycopg2
0 upgraded, 4 newly installed, 0 to remove and 10 not upgraded.Setting up libpq5 (9.3.4-1) ...
Setting up python3-psycopg2 (2.4.5-1build5) ...
Setting up apache2 (2.4.7-1ubuntu4) ...
* Restarting web server apache2
Setting up libapache2-mod-php5 (5.5.9+dfsg-1ubuntu4) ...
php5_invoke: Enable module pdo_sqlite for apache2 SAPI
php5_invoke: Enable module opcache for apache2 SAPI
php5_invoke: Enable module readline for apache2 SAPI
php5_invoke: Enable module json for apache2 SAPI
php5_invoke: Enable module sqlite3 for apache2 SAPI
php5_invoke: Enable module pdo for apache2 SAPI
apache2_invoke: Enable module php5
* Restarting web server apache2
Setting up xplico (1.1.0-14.04) ...
Installing new version of config file /etc/apache2/sites-available/xplico ...
Installing new version of config file /etc/init.d/xplico ...
Module php5 already enabled
Module rewrite already enabled
* Starting Xplico - Done! And those [OK] tags I saw in the process were very comforting.
- I then relaunched Firefox using a custom profile setting I have configured for Xplico usage and browsed to “http://localhost:9876/users/login”
- Looking like this may turn out well!
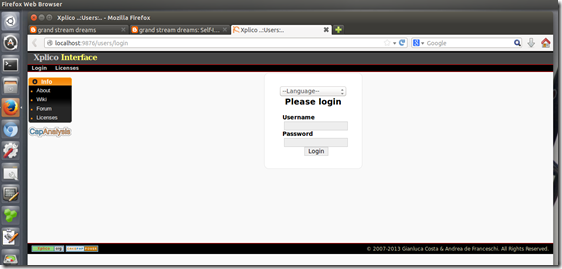
- Logging in and looking at my testing “cases” everything was back to normal again. Sweet!
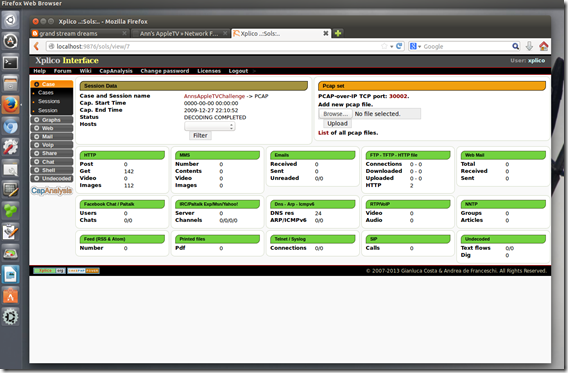
Note: PCAP file shown above collected from Network Forensics Puzzle Contest site; contest #3. - Next I logged in as admin to check out the installation details to confirm Xplico was 1.1.0
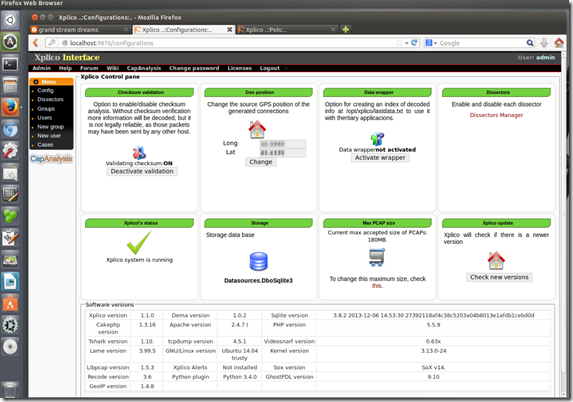
- Yep! It’s a little hard to see there but here you go.
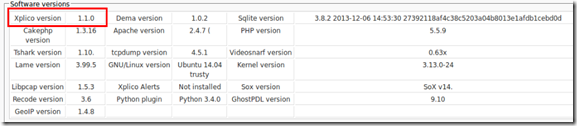
- All is well.
Xplico 1.1.0 is now running nicely in my Ubuntu 14.04 LTS virtual machine.
I’m even more wiser for the process thanks to the kindness of the developer.
I’ve got another blog post to add to the (eventual) GSD Xplico mega post that I keep collecting more material for.
All is well in the world!
Cheers!
Claus Valca
P.S. More images from the “xplico_1.1.0-14.04_i386.deb” deb package details when it was all said and done for the curious
![Xplico 1.0.0 [Running] - Oracle VM VirtualBox_2014-04-26_10-18-32 Xplico 1.0.0 [Running] - Oracle VM VirtualBox_2014-04-26_10-18-32](http://lh5.ggpht.com/-c_xzaNebP-Q/U1w8SxgVkYI/AAAAAAAABqo/m5zZmgXyO8M/Xplico%2525201.0.0%252520%25255BRunning%25255D%252520-%252520Oracle%252520VM%252520VirtualBox_2014-04-26_10-18-32%25255B4%25255D.png?imgmax=800)


![Xplico 1.0.0 [Running] - Oracle VM VirtualBox_2014-04-26_10-18-06 Xplico 1.0.0 [Running] - Oracle VM VirtualBox_2014-04-26_10-18-06](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiJALQnaKo_X8PPHs4HLkQGb_MA0reRXPqBqwztj2uwp4yOx1_AoN7OQMe3xlzgR7CG-R_V-OLRDq6gteIv_O2wiHvFZtSyQGxiOIdW6h9J0TwNi388z2XRS_rReT8TiKOl7hOp/?imgmax=800)