I’ve been running the Microsoft Enhanced Mitigation Experience Toolkit (now at version 4.1) for some time on all our home systems.
- Microsoft's EMET v 4.0 Released … in case you missed it - GSD Blog
- Microsoft's EMET v 4.1 Released … in case you missed it - GSD Blog
So with news of new threats that seemed to successfully bypass the EMET protections…
- New attack completely bypasses Microsoft zero-day protection app | Ars Technica
- Attack code bypasses Microsoft zero-day protection software | ZDNet
- Microsoft EMET's protections can be bypassed, researchers show
…I was excited to see that a new “technical preview” release of EMET 5.0 was available.
- Announcing EMET 5.0 Technical Preview - Security Research & Defense blog
- BETA: Enhanced Mitigation Experience Toolkit (EMET) v5.0 Technical Preview - Kurt Shintaku's Blog
- Enhanced Mitigation Experience Toolkit - EMET - TechNet Security
- Download Enhanced Mitigation Experience Toolkit 5.0 Tech Preview - Official Microsoft Download Center
Now I’ve been running EMET since at least back from June 2013, and have seen or heard nary a peep from it. I’m not complaining. That’s a good thing. I’m just running it with the standard default settings selected at installation.
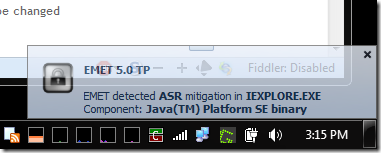
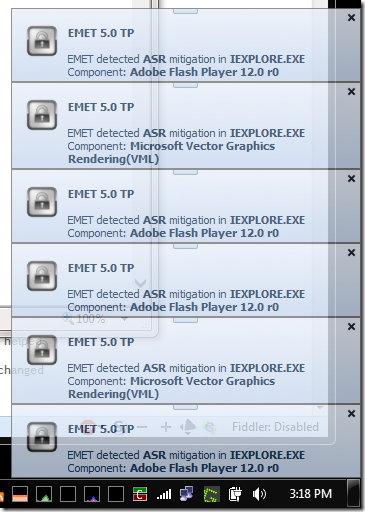
Strangely enough, this weekend, using EMET 5.0 TP I saw my very first alert occur!
For whatever reason, when I use Internet Explorer 11 I find that this EMET 5.0 TP version is particularly active spotting and blocking potential gotcha’s.
I can’t wait to see what the final EMET 5.0 will do when it finally comes out.
…an ounce of protection…
Cheers,
Claus Valca.

No comments:
Post a Comment