Ooooh! Guess who found a fun Word of the Day source?
Post XP SP3 Install Details - Not The Usual Hype
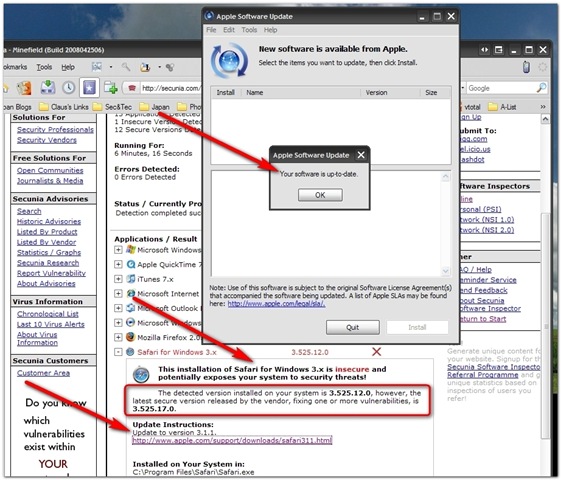
If all goes well, on Tuesday I will be able to manually download XP SP3 from the Microsoft Download Center. I suppose I could also kick off a manual Windows Update session as well and go looking for it, but my thinking is that I can grab it from the Download Center, then copy to USB for quicker deployment of other systems. While there was a bit of a stampede for Vista SP1, I expect a major server crush for XP SP3, especially considering how many folks have XP installed (corporately and at home).
Here are some more off-the-beaten-patch article concerning what's coming with XP SP3 that sysadmins might find interesting to consider:
Windows XP SP3, What You Can Expect - Bits from Bill - Bill Pytlovany used features in his own WinPatrol product to look for any system changes detected during installation.
Included were some "RunOnce" startup files to clean up registry entries used during the update process, a toolbar extension, and four Vista services ported over to XP. Bill's blog post goes into details on the items and actions discovered.
Windows XP SP3: Pretty damn good actually. Windows Live Installer: Sucks like a vacuum - Someone Else Blog - Robert Moir, someone I consider to be a pretty balanced blogger on Microsoft and Windows reports a positive post-XP SP3 installation process. He did include it as part of a fresh system installation of his desktop. Unfortunately, Robert has some choice words to use in assessing his experience with the Windows "Live" component installer. While I haven't had any problems with it, I find it a quirky method for Microsoft to use as the mechanism to install some very good applications. Come on, Redmond, drop this "suite installer" mentality and just provide some individual downloadable components. Tastes a bit bitter to some of us.
IE Blog Posts of Note
Yep. Development of IE8 soldiers on. Forecast calls for tweaks, enhancements and improvements, but likely no sexy changes to the browsed used by the masses.
IEBlog : What Happened to Operation Aborted? - Changes in IE 8 will work to cut down a particular error message encountered while loading pages that run some problematic scripting code. The new change allows the error to be logged for review (by hard-core developers or page code explorers) while usual users will just be able to view the main page they had navigated to, blissfully unaware of the hiccup.
IEBlog : Give Your Eyes a Treat - Nice reminder (and How To) of changing the default font for the Command line. IEBlog recommends using their own font Consolas, and I must say it is world's better than the default raster font used; Lucida Console. Once you get Consolas on your system, just make a registry key change and either reboot or log-off/log-on, then change to Consolas in your Command Prompt properties Font list.
I myself personally choose to use the freeware command line utility program Console hosted over on SourceForge. A new version 2.00 Beta build 139 has been released last month. What I really like about Console is that is supports use of multiple tabbed sessions, text-editor like selection of text, window backgrounds, transparency options, quick font-change support, and different window style configurations. Note; for some reason, it seems to be blocked from executing by Sunbelt Software's Personal Firewall program (formerly known as Kerio). I never took the time to troubleshoot out the issue but suspect it might have something to do with the HIPS component of that firewall program.
I use Console almost exclusively now as my command-line window of choice, coupled with the font Inconsolata. Some folks report having some issue with discerning a difference between the letter "o" and the number "0" in Inconsolata. One clever user fixed it in the font utility FontForge. I tend to agree with that assessment and when time allows will give that technique a shot as well. Looks like a wicked-cool application but requires a bit of work to compile on a Windows system...
Speaking of IE...
Download Squad had a cross-link to a useful reference post by The How-To Geek: Troubleshooting Internet Explorer on Vista Locking Up or Running Slowly
That post reminds us that IE 7 has a "safe-mode" feature which launches IE without the add-on's running. It also shows how to disable particular add-on's (something I had to do in my initial foray with AVG Free version 8). You can reset the IE settings to default, and a few more "light" tips are tossed in as well at the end.
From the Toy Box...
WinPatrol 2008 has been released! - A wonderful tool to assist with locking down a system from malicious activity. Well regarded and highly recommended. I personally don't run WinPatrol, having other tools that I rely on for my daily use, but for someone starting out or dealing with problematic PC usage in a shared environment (ie, the kids keep messing around on the Web and borking the pc with malware...) it is definitely a well-recommended choice by many, including me. BillP Studios: WinPatrol - (free/$ versions).
Windows Incident Response: RegRipper Video Posted - I continue to "experiment" with use of the Harlan's RegRipper tool to parse out useful information from registry files. This post links to a great video showing not only how RegRipper is used, but how it can be used "remotely" to capture information out of a registry once teamed up with the F-Response tool. Cool indeed!
windowless virtual toys - (freeware) - Using a single executable, add one or hundreds of curious little "creatures" to your desktop for fun and amusement. These are quite fun, and may be the digital equivalent to the Pet Rock. Must have for any bored sysadmin. Spotted and reviewed over at freewaregenius.com.
RegToy - (freeware) - A few posts ago I pondered this new registry tweaking tool. Did we really need another one? Maybe. Lifehacker has provided a great collection of screen-shots from the utility to help you decide: Featured Windows Download: RegToy Tweaks Your PC Every Which Way. I added it to my pile of Windows XP/Vista tweaking tools kept at USB ready.
Take Ownership of Files in Vista - (tip post) - Cybernet News reminds us how to, well, take ownership of a file by using one of those tweaking tools to add this option to the right-click menu in Vista.
Free Color Pickers - (software list post) - Cybernet News provides a nice list of "color-pickers" to aid in figuring out just what color (code) is in use in a web-page, image, etc. I use ColorZIlla in Firefox, but grabbed these others just to play with; ColorPic, Color Cop, and ColorMania. The post also has some links to on-line color tools. A commenter also suggested a great freeware tool from Veign called Pixeur. Veign has quite a nice collection of resources worth checking out while you are visiting.
Foxit PDF reader - (freeware) - This little guy has got to be my all time favorite of PDF replacements for Adobe Reader. The latest version adds a number of clever features, including "tabs". Always on top of things Cybernet News posts a nice roundup of all the new features, which I must say, are extensive!
10 great free downloads for your network - (list via ComputerWorld) - Nicely composed selection of networking tools that you might want to be familiar with. At the very least a few are actually useful for the average Joe. What makes this list fun is that it seeks to identify lesser-known free network utilities including RogueScanner, NetBrute Scanner, Network Notepad, and Advanced Net Tools (ANT).
The Best, Free Alternatives to Nero CD/DVD Burner - (list via makeuseof.com) - Another great collection listing seven choice solutions for free CD and DVD burning.
This Week in Firefox Tips (Tinfoil Hats optional but stylish)
Make Firefox 3 Use Windows Vista Glass Like Internet Explorer Does :: the How-To Geek - Sure, Firefox rocks and is even being optimized for Vista visual integration with new icons. However, they haven't added Vista's "Glass" effect just yet. This post by the How-To Geek shows how to do just that. I haven't done this yet on my Vista machine, but it is coming...maybe next weekend?
Make Firefox more responsive when loading pages - Browser Tip - Download Squad - Pssst. Want to try a tip to allow you to access the page content a bit faster as it loads up without having to wait? Apparently it comes down to a coding option that (by default) instructs Firefox to ignore user input in browser in favor to concentrating processor priority to page rendering first. The fix is easy; just go into about:config and change the (should be present) content.switch.threshold key value down to 1000000 from the default 750000 value. Done! If you don't like the results, just change it back. If it isn't present for some reason, right-click and add it in as a new "Integer" item. Comments on both sites linked, while light, have been positive. My experiences have been as well.
Knock, Knock, It's the FBI - (PC World Business Week post) - Hmmm. When I first saw this post I thought it was more tinfoil-hat in nature. But after I had re-read it a couple of times from a system administrator's (and parental unit) perspective, there might just be something here to consider. Grandpa was and commended FBI agent and I have only the highest regard for the field agents of the FBI. Heck, I even applied for a job with them way back when Grandpa was still around and I was a bit younger. Although I am less supportive of some recent policy decisions, however well intended, that are being made of late over there.
Anyway, I digress.
What is disconcerting is that by accessing a single web page, by purpose or accident, a world of hurt could come knocking down your door; at work or at home. If this (or other examples) actually become the norm, it may have a chilling impact and strong repercussions across the Internet, and the way we interact with it at home, work and across America. I'm now deeply ambivalent about this. Sure, those who don't haven't done anything wrong don't need to worry. Or do they?
See, that article by Network World writer Mark Gibbs does make two important points that most readers of the article are sure to have missed as they are down near the end past all the "sexy" FBI raid details:
Now, this is interesting for a number of reasons that should worry all of us in the IT industry. First, there's the issue of intent. It turns out that by simply accessing one of these links you are de facto, presumed guilty by your IP address being the proximate cause.
The fact that the action might not have been done by you personally is, apparently, not an issue. This makes running an open Wi-Fi access point completely inadvisable. And when your friends come over and ask to check their e-mail, the answer has got to be "no." And you'd better have in-depth Internet filtering for your kids.
The second issue concerns browser add-ons that attempt to pre-cache the content of links on a page. These add-ons are to improve perceived performance, but imagine that you run a Web search and wind up on a page that links to one of these FBI honeypots: Your browser will access the link and, unless you are masking what you do through something like the Tor network, the Feds will get your IP address. Before you know what's going on, there will be a knock on your door, you'll be hurled to the ground, cuffed, Mirandized, and all of your computer gear, financial records and leftover Chinese food will be en route to the local FBI office.
But what if an employee's browser pre-caches the contents of one of these FBI links, or the employee actually clicks on it? Can you imagine the chaos and insanity that would result from the FBI paying your company a visit? Work would grind to a halt, PCs and other gear would be impounded, records taken and your business would be dead in the water.
What caught my attention was the bit about "browser add-ons that pre-cache the content of links on a page." Mark didn't call names, but I know at least one browser he is talking about and at least one popular Firefox Add-on that can do that. Yep, Firefox is the browser and Fasterfox is the Add-on.
As Mark points out, we aren't talking about law-breakers who purposely troll for illegal content off the Web. We are considering the poor sap who puts in an unfortunate choice of terms in Google Search and pulls up clearly illicit material. If he/she is using Firefox, Google and Firefox will team up (by default) to do a pre-load of the top search result into the Mozilla browser cache.
While generally handy, this indeed may trigger a "hit" by the FBI honeypot trap. Who knows for sure?
This has been known by some for some time, at least back in March 2005 as this ZDNet article details: Google enhances search for Firefox users - ZDNet.co.uk
Want oodles of details?
- Google Help : Search Features - Results Prefetching
- Link prefetching FAQ - Mozilla Developer Center (MDC)
It's not limited to just Google, however. Just about any website coder who is familiar with link prefetching can code it to occur to their desire and whim.
As the article and these details indicate, you may indeed end up with cookies and content in your browser cache and on your drive that you didn't even actually click-through to.
And yes, both the article and the MDC FAQ point out, a good and knowledgeable reviewer of pc forensic expert should/might be able to distinguish them from "real" click-throughs based on a special header. Course, there's no guarantee that's what you will end up with in the courts....
So if you are the tin-foil hat type, or just want to try to do some quick and basic prefetching avoidance, what are you to do if you use Firefox?
Easy: Turn off prefetching. (via MDC)
Easier way via Cybernet News post tip:
If you don’t want Firefox to do this then you’ll have to manually go and disable it:
- In the Firefox Address Bar type about:config and press Enter.
- Find the option that is named network.prefetch-next and double-click on it.
- Change the value to false.
You might actually see some speedup in your web-surfing if you are bandwidth-challenged.
Certainly an issue worth considering.
Cheers!
--Claus