About a month ago, one of our network analysts brought the following freeware malware-scanner program to my attention:
Free spyware removal and spyware protection - Spyware Terminator
He had been using it for a while and really liked it.
I generally stick with a close-knit group of anti-ware (Dwight lingo) programs so I was a bit hesitant to jump on a new one I haven't heard of before...but that's how you learn...by trying new things.
Some History First
I wanted to do some research on this program before firing it up on my systems.
I searched around and read a number of user-comment software reviews.
File Forum had a very strong and balanced thread, with a few folks concerned that it wasn't a legit application, and a slew of others in support of it. FileForum | Reviews of Spyware Terminator.
It's listed over at filehippo which is a download site I trust.
Posters at the Download.com download link for the application seemed positive.
I didn't see anything that really caused me alarm.
It had been previously listed on Spyware Warrior's Rouge/Suspect Anti-Spyware program list, but has now been de-listed.
That, coupled with some additional reading via a Google Blog search on the program left me feeling pretty secure that I wasn't going to hammered with a rouge anti-spyware product.
Basic Features
Here are some basic features Spyware Terminator offers:
- Real-time protection (if optionally enabled).
- Quarantining of suspect files (it's always good to quarantine before removing, just to be safe).
- Setting of manual and scheduled scans.
- Setting of manual and scheduled updates.
- A (generally) friendly user interface.
- Free for personal and commercial use (a $ version with network administration support also available).
- Allows for fast,full, or customized scans.
- Provides detailed scan-result reporting.
- Supports integration with the free and open-source anti-virus application ClamAV.
- On-boot malware removal routine if needed.
- Pre-defined "profile" configuration...so protection can be adjusted for user type.
- An integrated "locked-file" removal tool. (See my list for more stand-alone locked file tools).
- Integrated single-file malware scanning via the Explorer right-click context menu.
Download sites report it is compatible with Windows 98/Me/2000/XP.
I haven't tried it yet with Vista and cannot find any thing specifically on Spyware Terminator's website that says it is or isn't Vista compatible. When I get done testing on our Vista laptop, I will drop an update in the post or in the comments.
Download and Installation
First you have to choose which download version you want. Spyware Terminator (Free) comes in two flavors:
Spyware Terminator & Web Security Guard (9.96 MB) - This version packs all of the features of Spyware Terminator along with anti-virus protection included and an web-watcher process to protect users from loading hostile websites.
Spyware Terminator (3.33 MB) - The plain version without the web-monitoring program.
I went with the plain version.
Upon running the installer, one is presented with the Crawler EULA, privacy policy, et.al. Seems pretty standard fare and works hard to try to distance itself from it's prior problematic history of associations.
Once installed you are presented with the option to set it to "scan for spyware," "protect against spyware" (which will then install the Real-time Shield), or "Protect against spyware and viruses" by installing Real-time Shield and Clam AV.
I just use these as on-demand scanners..so I picked Scan for Spyware. Since I downloaded just the basic version, I wonder if selecting the "Protect against spyware and viruses" option would then require an update download to get the additional elements?
Under the Hood
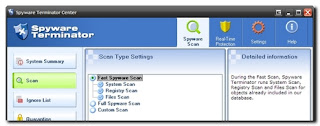
The nice and clean user interface presents you with the following options under the Spyware Scan tab:
System Summary - which provides info on your program version and application news.
Scan - where you can select a fast, full, or custom scan.
Ignore List - where ignored items are recorded.
Quarantine - which displays items you have located and selected to keep around safely before removing.
Update - where you can manually update the application.
Utilities - to restore system defaults, roll back to a system restore point, analyze a file (see if it runs, if it has related registry items, and property information), or remove a file (delete or delete-locked file).
The Real-time Protection tab allows you to enable and customize the settings for application guarding, system guarding, and Internet guarding, along with enabling Host Intrusion Prevention System (HIPS) protection.
The Settings tab lets you enable/disable reporting back to the Spyware Terminator mother-ship servers, customize scans to look for cookies, invalid items, unreadable files, alternate file streams and use the System Restore, schedule automatic scan times and updates, and integrate ClamAV.
Fire in the Hole!
I fired up and ran a manual "quick" scan of my system, and watched the program begin.
It ran a scan of all the running processes, registry items and key files.
"Fast" scan time took approximately 3 minutes on my XP Home system.
It scanned over 11,000 objects on my system and found 152 items of note...none "critical."
Once the results were displayed, things got really interesting.
Is this Good or Bad?
The scan results are reported on a four-tabbed view.
The first displays Threats...on my system these were (as expected) just some miscellaneous tracking cookies with a low threat rating. Had additional malware items been found, they would have also been listed along with an elevated threat-level symbol.
What I found very nice about this is that they included the file-path to the located files, so if I wanted to do more manual investigation on my part, I could quickly track the suspicious items down. I can also select and report false positives to the vendor directly off this screen (very nice!) and move the selected item(s) to quarantine as well as delete them. All handy features.
The second tab displays Safe Software. It appears that Spyware Terminator uses an internal "whitelist" database to list programs, services, and other files it locates and knows are safe. These may be expanded to view the location detail as well as a brief abstract about the item in review and can be placed in quarantine if desired.
The third tab displays any "Unknown" Software. These would be applications, files and registry items that haven't made the "whitelist" but aren't in the "blacklist" either. You may select the items here and set them for quarantine, ignore, add to the "whitelist", or designate as a threat. You may also sent them to the vendor for "professional" review.
The final tab is a scan report. You may copy the report to the clipboard which would list processes, Startup items, toolbars, BHO's, IE bars, IE Extensions, Services, Protocols, Winsocks, Uninstallers, Start Menu items, Desktop Items, Favorites, Cookies, Registry items, and key files scanned and their file locations.
Whew!
Is Spyware Terminator Portable?
Well....kinda.
Note: This is not supported by Spyware Terminator, and by design the program really isn't intended to be run this way. Just want to pass this on to other sysadmins who fight malware at work off USB sticks on the fly.
Since I have to travel to a bunch of systems to clean them of malware, I wondered if the program could be successfully run off a USB stick.
So I copied the installed program folder and went to another pc that it wasn't installed on and gave it a try.
Yep! Worked like a charm. Obviously you will want to set the options to not run scheduled updates/scans if you do so, nor will you probably want to enable the "Real-time" protection. I'd recommend you disable these prior to copying the program folder to your USB stick.
Only one problem. Once the program was ended and the USB stick removed, the program left the Windows right-click context menu item for individual file scans still in place.
You won't want to be leaving litter like this around when you use this program in an unsupported "portable-mode."
What to do?
Spyware Terminator Registry Key Fix
I located the key causing this behavior and wrote a simple registry key file that when executed removes the key in question and takes out the context menu item (as tested on my XP systems at least).
- Open notepad and copy the following two lines of text into the file. (Note: the second line is a single line):
Windows Registry Editor Version 5.00
[-HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{BD88A479-9623-4897-8546-BC62B9628F44}]
- Save the file with the following name "RemoveSPTKey.reg" (or whatever you want, just be sure to save it with the .reg extension."
- Put that saved file in the program file with your other files.
- Run Spyware Terminator and do the malware busting and tracking cookie crumbling.
- Once done, close the program.
- Now run the registry file to remove the key from the local registry.
- Gone!
More information on how to use RegEdit, batch files, and adding and removing registry keys: Use REGEDIT to add, read or delete registry values.
And as always...remove registry keys from your own system at your own risk!
Charitable Giving
Spyware Terminator also offers a free license for Non-Profit Organizations (schools, government organizations, churches, charities, etc...) which includes both the primary program as well as the (otherwise $) network administration tool so you can manage all the installed clients across workstations. Very classy move!
Final Recommendation
I really like this application. It is fast and has a wide-range of features that will compliment other anti-malware applications already on the market. The included tools and utilities should greatly help leverage the application.
None of my home systems have any malware to test its true removal/repair capabilities. Just nuisance cookies. So I still can't say how it compares to actually removing easy-to-difficult malware infections. In those cases, I still will be using it as one of many of my trusted anti-malware tools I toss at an infected system. And I haven't found an anti-ware product yet that can 100% clean an infected system. Everyone I've run into has still required a certain amount of detailed hands-on manual work to remove some stubborn files/programs/processes to get it completely cleaned up.
I've been running it for a while and haven't found any ill-effects from it's installation and use on my own systems.
I do have mixed feelings recommending this program to a new or beginning-level user without some supervision or training by someone familiar with the program first.
The only reason I say so, is because on my system, the scan results listed seven items under the "unknown software" tab. I knew these were all safe and (in fact) required programs and files for healthy operation of my system.
My fear would be that an inexperienced user might try to remove or quarantine these items by mistake and end up tanking their system.
However that is also one of the strengths of this program that I like, so I can't say it doesn't need to be right were it is. Just decide and understand carefully before acting on the items listed there, and if in doubt, don't touch-em.
Overall...Valca Recommended
Happy (malware) Hunting!
--Claus