I've been noticing a slow increase in the number of spam one of my Gmail accounts has been getting. Other users have also been reporting this trend.
Luckily, Gmail has some pretty good filters and has caught all the crud that has hit my account. I still go through it occasionally, just to make sure something didn't accidentally get caught by the filters.
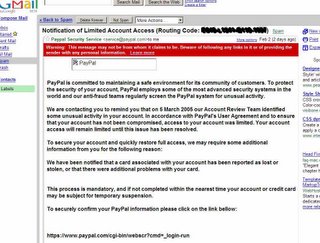
Imagine my surprise when I saw I got 3 (THREE!) notices from PayPal that they caught a bad transaction back in 2005 and needed me to update my account or else it would be closed. GASP! SHUT DOWN MY PAYPAL ACCOUNT! OH NO! I BETTER GO AND FIX IT RIGHT AWAY! LET ME GIVE THEM ALL MY PAYPAL ACCOUNT INFORMATION SO THEY CAN PROTECT ME!
Lucky for me they provided a link to their secure site so I could log in....but wait....something was tickling my brain....was it:
1) The fact that I never had an PayPal account associated with that Gmail account? or,
2) The HONKIN' BIG BOLD RED Warning Gmail provided me on the email header?
Actually, for me, it was #1. But the more I looked at it, I thought #2 was really neat.
Also, this was just too good to pass up as an anti-phishing lesson. Now I know most of you are way too net-savvy to get caught by these things. In fact, IE7 incorporates some anti-phishing technology in their latest build. However, some of you may find this interesting.
First, I switched over and viewed the source-code of this HTML formatted email. The first place I wanted to examine was the "login-link" they provided to enable me to log into my PayPal's account site.
Luckily, Gmail has some pretty good filters and has caught all the crud that has hit my account. I still go through it occasionally, just to make sure something didn't accidentally get caught by the filters.
Imagine my surprise when I saw I got 3 (THREE!) notices from PayPal that they caught a bad transaction back in 2005 and needed me to update my account or else it would be closed. GASP! SHUT DOWN MY PAYPAL ACCOUNT! OH NO! I BETTER GO AND FIX IT RIGHT AWAY! LET ME GIVE THEM ALL MY PAYPAL ACCOUNT INFORMATION SO THEY CAN PROTECT ME!
Lucky for me they provided a link to their secure site so I could log in....but wait....something was tickling my brain....was it:
1) The fact that I never had an PayPal account associated with that Gmail account? or,
2) The HONKIN' BIG BOLD RED Warning Gmail provided me on the email header?
Actually, for me, it was #1. But the more I looked at it, I thought #2 was really neat.
Also, this was just too good to pass up as an anti-phishing lesson. Now I know most of you are way too net-savvy to get caught by these things. In fact, IE7 incorporates some anti-phishing technology in their latest build. However, some of you may find this interesting.
First, I switched over and viewed the source-code of this HTML formatted email. The first place I wanted to examine was the "login-link" they provided to enable me to log into my PayPal's account site.
The code was crafted to display the following (legitimate) secure PayPal address:
https://www.paypal.com/cgi-bin/webscr?cmd=3D_login-run=
https://www.paypal.com/cgi-bin/webscr?cmd=3D_login-run=
However, it had a href code to actual send the user to the following site: (Note: IP removed to protect the silly) http://xxx.x.xx.xxx/~mrtg/secured.transaction.com/webscr.ph=p?cmd=3D_login-run
Interesting. So anyone who decided to ignore Gmail's bold warning, and click through to what appeared to be a secure legitimate PayPal site would instead be routed to these, um, gentlemen.
OK, one IP address collected, what else? Ah! The Email-header!
As I posted before, the folks at Onimoto have a simple but good guide on how to trace an Email; including for Gmail. A quick search of the headers one of the Emails in question revealed the following (sanitized):
X-Gmail-Received: <<SNIPPED>> Delivered-To: << SNIPPED>>@gmail.com Received: by xx.xx.xxx.xx with SMTP id << >>; Thu, 2 Feb 2006 05:57:59 -0800 (PST) Received: by xx.xx.xxx.xx with SMTP id << >>; Thu, 02 Feb 2006 05:57:59 -0800 (PST) Return-Path: Received: from xx.xx.xxx.xx (<< >>.dsl.sndg02.pacbell.net [xx.xx.xxx.xx]) by mx.gmail.com with SMTP id << >>; Thu, 02 Feb 2006 05:57:59 -0800 (PST) Received-SPF: softfail (gmail.com: domain of transitioning service@paypal.com does not designate xx.xx.xxx.xx as permitted sender) Received: from xx.xx.xxx.xx by ; Thu, 02 Feb 2006 15:52:47 +0200 Message-ID: < << >>@comcast.net> From: "Paypal Security Service" Reply-To: "Paypal Security Service" <> To: << >>@gmail.com Subject: Notification of Limited Account Access (Routing Code: << >>) Date: Thu, 02 Feb 2006 12:54:47 -0100 X-Mailer: Microsoft Outlook Express 6.00.2600.0000 MIME-Version: 1.0 Content-Type: multipart/alternative; boundary="--<< >>" X-Priority: 1 X-MSMail-Priority: High
This contained an IP trail of the bounces the email took from the sender to my Gmail account.
Once I had all the IP's noted, I was curious where the location of the sender was. I browsed over to ARIN (American Registry for Internet Numbers) and started entering the IP's I noted. Very quickly it became evident that the sender was based in Europe. It bounced from there through some email routers in California then dropped into my account. Fascinating!
Now what? Well I could just flush the emails, but that was too kind. I have to deal with this crap at work so I flipped over to PayPal. Following their links, the Good Guys of PayPal have set up a really nice Security Center web-page that explains phishing. I suspect they deal with this a lot. They actually ask users to forward these phishing Emails to them for review and response. Wow! Well, let's see what they would do with these messages. I copied them and forwarded them--headers and all.
To my delight and surprise, a few days later I got two (very personal) Email responses back from them! They confirmed (surprise-surprise) that they were indeed false Emails--not from PayPay. And, that they were actively working on getting those IP addresses shut down! Sweet work PayPal.
So, lesson to the wise. Keep your eyes open and your brains turned on when it comes to these kinds of Emails that will eventually trickle into your Inbox/Spambox from time to time. Don't panic. If you don't have time, just delete them and move on. If you want to do more, practice picking them apart and see if the Good Guy site has a place to report them. You're doing a good deed, if you do.
A few more Phishing Resources:
Phishing via the Wikipedia
How Not to Get Hooked via the US-FTC (really clever title there BTW guys...)
Help prevent identity theft from phishing scams via Microsoft
Anti-Phishing Blog
See you in the skies,
--Claus
OK, one IP address collected, what else? Ah! The Email-header!
As I posted before, the folks at Onimoto have a simple but good guide on how to trace an Email; including for Gmail. A quick search of the headers one of the Emails in question revealed the following (sanitized):
X-Gmail-Received: <<
No comments:
Post a Comment